Comprehensive IT.
Total peace of mind.
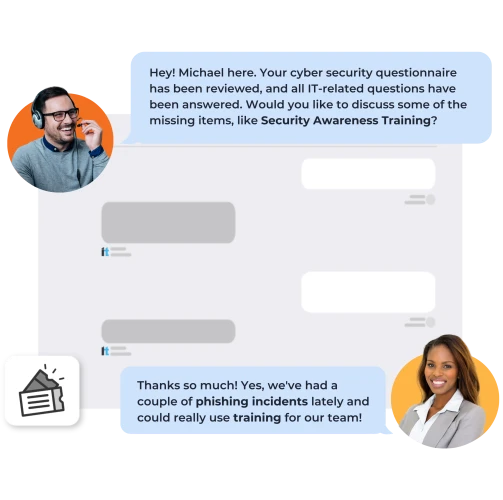
ITSG helps small business owners like you save time and money doing your helpdesk and cyber security by providing dedicated experts and battle tested software from industry giants - so you can focus on growing your business.
Trusted to resolve 2+ million support tickets since 2006
91 | Net Promoter Score®

2+ million | Tickets Resolved

98.8% | Satisfaction Rating

4 secs. | Average wait call time

94.53% | Same Day Resolution
Your one-stop shop for IT solutions
Experience a seamless tech journey with a single destination for all your IT needs. From consulting to implementation, support, and growth strategies, we've got you covered. Simplify complexity, optimize resources, and fuel your success with our comprehensive suite of IT solutions. Make technology work for you with Your One-Stop Shop for IT Solutions.
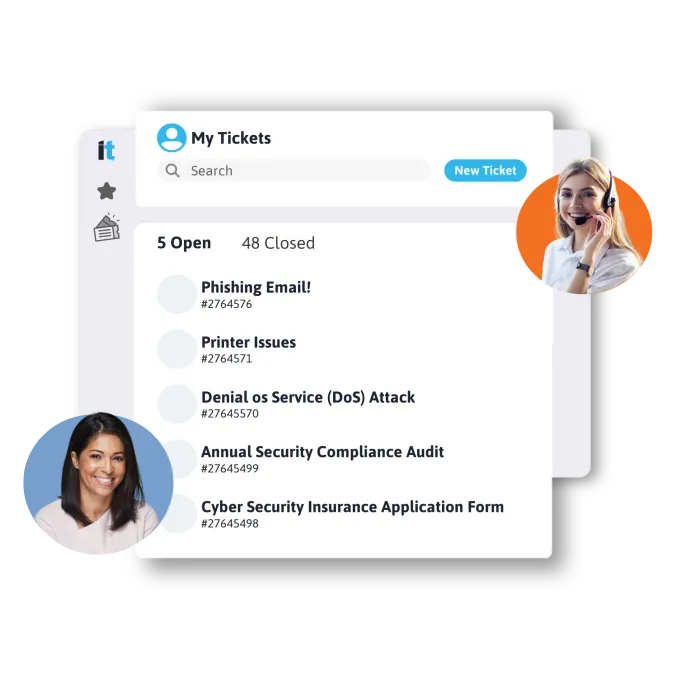
Unlimited Help Desk Support
24/7 expert assistance via phone, email, or chat. Dedicated team, remote troubleshooting, software/hardware help, user training. Quick responses, proactive monitoring, scalable for growth. Keep operations smooth with reliable, accessible IT support.
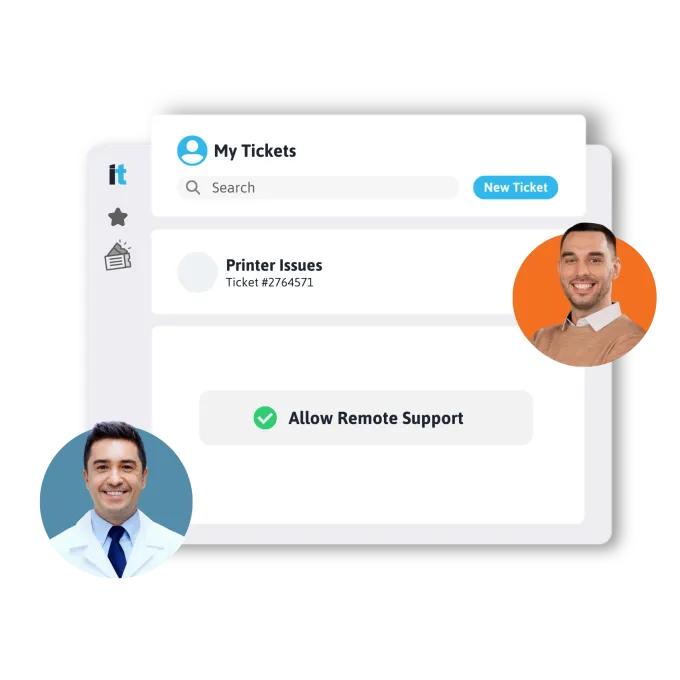
Remote IT Support
Instant, secure remote assistance for technical issues. Skilled experts troubleshoot software, hardware, and more. Swift problem-solving, proactive monitoring, scalable for future needs. Ensure seamless operations with remote IT expertise.
24/7 Security and System Monitoring
Continuous vigilance for your network and data. Round-the-clock protection against threats. Real-time monitoring, rapid threat response, scalable for growth. Safeguard your assets with constant security and system oversight.
Your Fully Staffed IT Department
Empower your business with a dedicated team of skilled IT professionals. Unparalleled expertise at your fingertips, offering comprehensive solutions from troubleshooting to strategic planning. Enjoy top-tier support, cost-effectiveness, and innovation all in one package. Elevate your technology game with Your Fully Staffed IT Department.

Stay Informed:

Why You Can’t Ignore Single Sign On (SSO) for Enhanced Cybersecurity
In today’s digital age, businesses are facing an increasing number of challenges when it comes to managing user identities and
Alternatives to Active Directory: Can Azure AD be a Replacement?
Many businesses are moving into the cloud, and with good reason. Cloud infrastructure and apps can make businesses more agile,

What is a Virtual CIO (vCIO)? Gain The Advantage with a Tech Expert!
The owner and/or CEO of your average small to mid-sized business is often spread too thin. When starting a business
Resources

10 Questions You Need To Ask When Interviewing IT Professionals
Sifting through resumes to find a perfect fit can be daunting. It is hard to recognize good talent from just reading their resume.

5 Must-Have IT Job Descriptions to Jump Start Your Hiring Process
Finding the right IT Specialist can be more challenging. We’ve created five must-have job descriptions for the most commonly needed IT employees to help you

Understanding AI Maturity
Artificial Intelligence (AI) is revolutionizing SMBs. We’ll help you understand the different maturity levels, and how leveraging AI can become the winning strategy to propel
Get Your IT Survival Guide
Cloud Native Managed IT Solutions
IT support designed for your unique industry challenges, business applications, and technology.
Consumer Goods
Financial Services
Healthcare & Medical Offices
Legal & Law Practices
Manufacturing
Media & Entertainment
Leverage Cloud Native Cybersecurity Expertise
Beyond The Perimeter
You have questions, we have answers
We partner with the world's best








