Our Platform
A Unified Approach to Cybersecurity
At Next Perimeter, we offer a seamless, all-in-one cybersecurity platform that covers all aspects of your digital environment. From protecting your network and applications, to ensuring compliance and addressing threats, we're here to deliver the solution you need to safeguard your business.
Built on a foundation of Zero Trust and powered by AI, our platform integrates with you existing systems to provide end-to-end security that grows with your organization.
Effortless Security for a Modern Workforce, No VPN Required
Empower your team to work securely from any location with seamless access to corporate resources. Next Perimeter’s platform ensures only the right people access your network, verifying identity and context at every step. Adapt to evolving threats while maintaining productivity, whether your team is in the office or remote.
Holistic Protection Across Your Digital Environment
Our platform offers comprehensive coverage, ensuring that every part of your network, applications, and data is secure.
With integrated solutions for network, SaaS, endpoint security, and comprehensive threat detection, Next Perimeter provides a unified defense against even the most sophisticated cyber threats.
Enhanced Compliance and Simplified Management
Navigate the complexities of regulatory compliance with ease. Our platform includes tools and features that streamline compliance management, from automated reporting to continuous monitoring.
We’re here to help you meet industry standards while focusing on your core business objectives.
Scalable Solutions Tailored to Your Needs
Whether you’re a small business or growing an enterprise, Next Perimeter’s platform adapts to your needs.
Our flexible architecture allows for easy scalability, ensuring that your security posture evolves alongside your business without compromising on protection or performance.

97 Net Promoter Score®

2+ Million Incidents Resolved

4.9 Stars Average Ratings

4 Minute Average MTA

94.53% Same Day Resolution
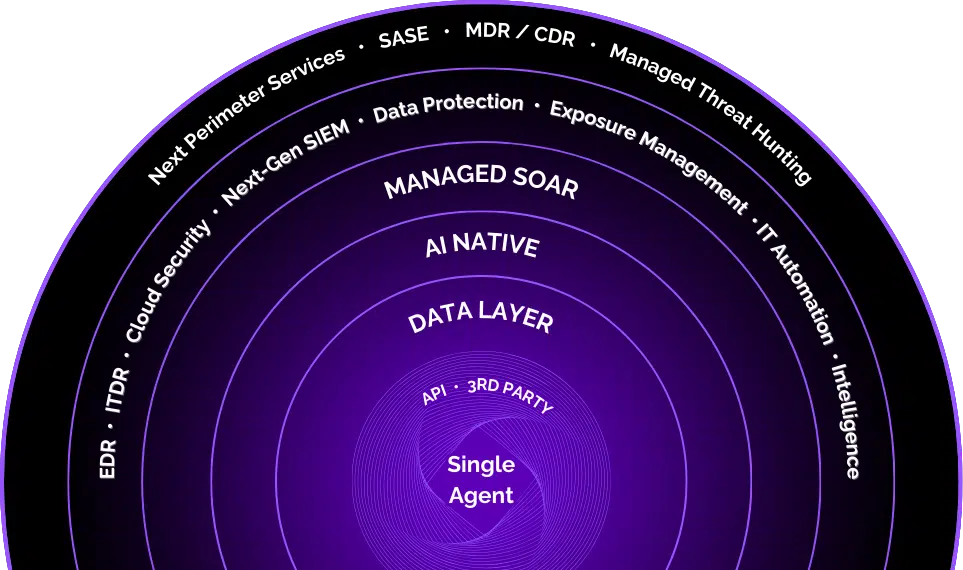
Achieve Total Security with Our Single-Agent Solution
Simplify your cybersecurity with a unified platform that combines advanced threat detection, data protection, and cloud security, ensuring seamless and comprehensive protection.
Effortless, Secure Connectivity
Network as a Service
Experience seamless, reliable connectivity without the hassle of traditional hardware. Our cloud-based Network as a Service simplified management, reduced costs, and scales with your business, ensuring your network is always protected and optimized for performance.

Seamless Cloud Application Security
SaaS Security
Secure your cloud applications effortlessly. Our SaaS Security solution safeguards your data with integrated identity management and real-time threat detection, all while maintaining compliance and boosting productivity across platforms like Microsoft 365 and Google Workspace.

24/7 Threat Detection
Managed Extended Detection & Response (MXDR)
Stay protected around-the-clock with our MXDR solution, combining real-time threat detection with expert analysis. We reduce alert fatigue and provide clear, actionable insights, so you can focus on your business while we handle the security.

Real-Time Monitoring & Insights
SIEM & Threat Detection
Gain peace of mind with real-time threat monitoring and intelligence. Our SIEM solution offers continuous protection, customizable insights, and the flexibility to grow with your business, keeping you secure in an evolving digital landscape.

Native Integrations with the Apps that Keep Your Business Running









READY TO TRANSFORM YOUR CYBERSECURITY?
Switching to Next Perimeter is Simple, with No Downtime or Disruptions
1. Free Exploratory Consultation Call
Let’s dive into your specific needs, security challenges, and current technology set-up. We’ll collaborate with you to start crafting tailored solutions that align with your business goals.

2. Identity & Device Assessment
Our experts will begin developing a customized proposal for your unique environment. We’ll perform a thorough assessment to finalize the scope, ensuring every aspect of your digital security is covered.

3. Schedule Your Seamless Onboarding
With your approval, we’ll launch your onboarding process. Our all-in-one security solution will seamlessly integrate into your existing infrastructure, implemented by our expert team for a smooth transition.
