Software as a Service (SaaS) Security
Advanced Protection for Your SaaS Applications
Protect your business and cloud-based assets with a fortified digital workspace. Next Perimeter’s SaaS Security solutions safeguard your SaaS applications, ensuring your data remains secure, compliant, and accessible only to the right people.
A Safer SaaS Environment Without Sacrificing Productivity
Secure your SaaS applications with Next Perimeter and experience the benefits of a robust security posture. From real-time threat detection to streamlined access management, our solutions help you stay ahead of cyber threats while maintaining operational efficiency.
Shield Your Business from Cyber Threats and Risks
Stay ahead of evolving cyber threats with Next Perimeter’s AI-driven SaaS Security. Our 24/7 Security Operations Center (SOC) identifies and neutralizes risks in real-time, ensuring your business remains protected from malware, phishing, and insider threats.
Secure Customer Data and IP with Confidence
Enhance trust and credibility with Next Perimeter’s robust security protocols. Our advanced encryption, access controls, and data loss prevention measures ensure that sensitive information remains protected, giving you and your clients peace of mind.
Keep Your Company Running Smoothly
Ensure uninterrupted operations with our advanced security measures. As your business moves to cloud-based solutions, we help safeguard your critical functions from disruptions, data loss, and unauthorized access, so you can focus on growth.

97 Net Promoter Score®

2+ Million Incidents Resolved

4.9 Stars Average Rating

4 Minute Average MTA

94.53% Same Day Resolution
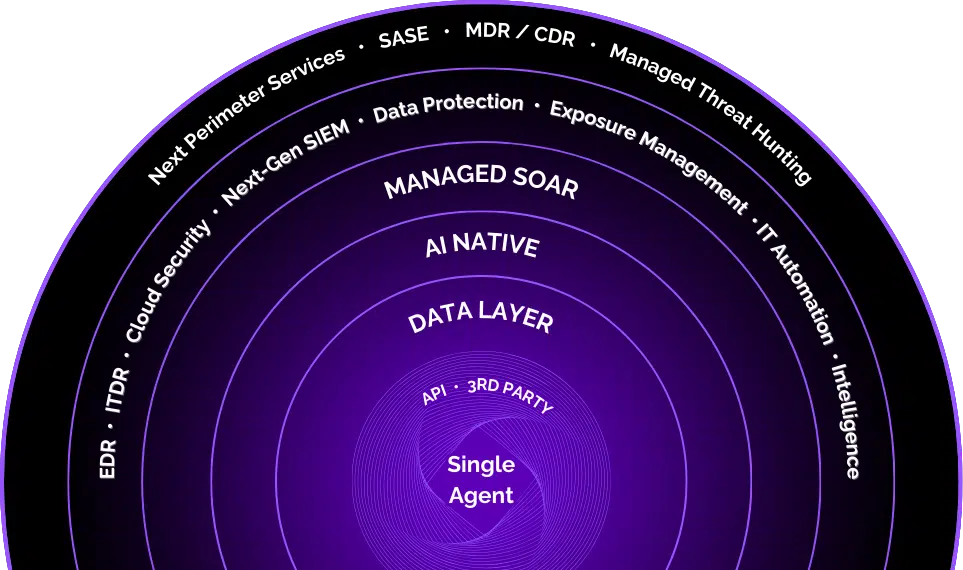
Achieve Total Security with Our Single-Agent Solution
Simplify your cybersecurity with a unified platform that combines advanced threat detection, data protection, and cloud security, ensuring seamless and comprehensive protection.
Identity and Access Management
Strengthen Access with Multi-Layered Security
Protect your SaaS environment by ensuring that only the right users have access to your applications. Our solution offers advanced identity and access management (IAM) features, including multi-factor authentication (MFA) and single sign-on (SSO).
These tools not only safeguard your data but also simplify the user experience by allowing secure, streamlined access across all your cloud applications.

Data Encryption and Protection
End-to-End Data Security You Can Trust
Protect your business’s sensitive information with Next Perimeter’s comprehensive data encryption solutions. Our approach includes endpoint encryption using trusted tools like Intune and BitLocker, ensuring your data is securely protected on devices and across your cloud environment.
With advanced encryption protocols, your critical information remains safeguarded against unauthorized access, helping you maintain compliance and reduce risks.

Threat Detection and Response
Detect and Mitigate Threats in Real-Time
Our solution leverages cutting-edge AI and machine learning to continuously monitor your environment, quickly identifying potential security incidents. When a threat is detected, automated response actions are triggered to contain and mitigate the risk before it can disrupt your operations.
Our 24/7 Security Operations Center (SOC) provides expert oversight, ensuring that every threat is addressed swiftly and effectively, minimizing any potential impact on your business.

Compliance and Audit Reporting
Simplify Compliance with Comprehensive Reporting
Our SaaS Security solution streamlines the process of generating detailed compliance reports, enabling you to meet industry standards and regulatory requirements with minimal effort.
Whether you need to demonstrate adherence to HIPAA, SOC2, or other regulations, our reporting tools provide clear, actionable insights that help you stay compliant and transparent.

Seamless Integration with Existing Tools
Unify Your Security Across All Platforms
Enhance your existing security infrastructure with seamless integration. Our platform is designed to work effortlessly with a wide range of security tools and technologies, enabling unified visibility and control across your entire environment.
Regardless of the existing security tools and systems your organization utilizes, our integration ensures that all components work together harmoniously, providing a comprehensive defense strategy that enhances both efficiency and security.

Native Integrations with the Apps that Keep Your Business Running









READY TO TRANSFORM YOUR CYBERSECURITY?
Switching to Next Perimeter is Simple, with No Downtime or Disruptions
1. Free Exploratory Consultation Call
Let’s dive into your specific needs, security challenges, and current technology set-up. We’ll collaborate with you to start crafting tailored solutions that align with your business goals.

2. Identity & Device Assessment
Our experts will begin developing a customized proposal for your unique environment. We’ll perform a thorough assessment to finalize the scope, ensuring every aspect of your digital security is covered.

3. Schedule Your Seamless Onboarding
With your approval, we’ll launch your onboarding process. Our all-in-one security solution will seamlessly integrate into your existing infrastructure, implemented by our expert team for a smooth transition.
Your Questions Answered: SaaS Security
Learn how Next Perimeter’s cloud-first SaaS Security solutions streamline and protect your digital environment.
What is Software as a Service (SaaS), and how does it benefit businesses?
Software as a Service (SaaS) is a cloud-based service where software applications are delivered over the internet. Instead of installing and maintaining software, businesses can access it via the web, reducing the need for on-premises hardware and infrastructure. SaaS offers flexibility, scalability, and cost-effectiveness, allowing businesses to focus on their core operations without worrying about software management.
What is SaaS Security (Software as a Service Security) and why is it important?
SaaS Security refers to the measures and protocols implemented to protect data and applications hosted in the cloud. It is essential for preventing data breaches, ensuring compliance with regulations, and safeguarding sensitive information. As businesses increasingly rely on SaaS solutions, robust security practices help mitigate risks associated with cyber threats and data loss.
What are the security standards for SaaS?
Security standards for SaaS providers include compliance with frameworks like ISO/IEC 27001, SOC 2, and GDPR, among others. These standards ensure that SaaS providers adhere to best practices in data protection, privacy, and security management. Certification under these standards indicates that a provider has undergone rigorous assessments and is committed to maintaining high security levels.
How do you ensure data security in SaaS?
To ensure data security in SaaS, businesses should choose providers that offer strong encryption methods, multi-factor authentication, regular security audits, and data backup and recovery solutions. It’s also important to have clear data governance policies and to regularly review and update access controls.
What is an example of SaaS security?
A common example of a SaaS security feature is multi-factor authentication (MFA). MFA adds an extra layer of security by requiring users to provide two or more verification factors to gain access to an application. This reduces the risk of unauthorized access, even if login credentials are compromised.
What are the common threats to SaaS applications?
Common threats to SaaS applications include phishing attacks, account hijacking, data breaches, insider threats, and DDoS attacks. These threats can compromise sensitive data, disrupt services, and cause significant financial and reputational damage. Implementing strong security measures and educating users are key to mitigating these risks.
How does SaaS compare to traditional software in terms of security?
SaaS often offers superior security compared to traditional on-premises software due to regular updates, dedicated security teams, and compliance with stringent industry standards. However, businesses must also ensure they implement strong security practices, such as access controls and data encryption, to complement the security measures provided by the SaaS vendor.
What role does data encryption play in SaaS security?
Data encryption is crucial in SaaS security as it protects sensitive information by converting it into a secure format that can only be accessed by authorized users with the correct decryption key. This prevents unauthorized access, even if the data is intercepted during transmission or at rest. Encryption helps protect both the integrity and confidentiality of data.
