SIEM and Threat Detection
Protect Your Business with Advanced Intelligence
Empower your organization with cutting-edge security tools that monitor, detect, and neutralize threats in real-time.
Next Perimeter's SIEM and threat detection offers retention-based billing with unlimited storage, so you only pay
for what you can control—how many devices you have and how long you retain events—without worrying about
log volume or storage limits.
Stay one step ahead of potential risks while keeping your data and operations secure.
Unlock the Power of Next-Gen Threat Detection with SIEM
Next Perimeter's advanced SIEM solutions provide comprehensive visibility and precise threat detection, ensuring your business stays secure in an increasingly complex digital landscape. Experience the power of advanced security and detection, designed to protect, adapt, and grow with your organization.
Comprehensive Monitoring and Threat Visibility
Stay ahead of potential threats with full visibility across your entire network with continuous scans and data analysis from all endpoints. With early detection, we can quickly respond to threats and protect your business from sophisticated cyber risks.
Reduced Alert Fatigue, Maximized Security
Next Perimeter’s SIEM solution prioritizes alerts to filter out false positives, ensuring that your team can focus only on genuine risks. This targeted approach reduces alert fatigue by prioritizing the detection of authentic cyber threats to your business.
Effortless Integration Designed for Your Growth
Effortlessly integrate our SIEM with your existing infrastructure, ensuring a smooth and hassle-free deployment. As your business scales, our solution evolves with you, providing consistent security at every stage of your business’ growth.

97 Net Promoter Score®

2+ Million Incidents Resolved

4.9 Stars Average Ratings

4 Minute Average MTA

94.53% Same Day Resolution
Achieve Total Security with Our Single-Agent Solution
Simplify your cybersecurity with a unified platform that combines advanced threat detection, data protection, and cloud security, ensuring seamless and comprehensive protection.
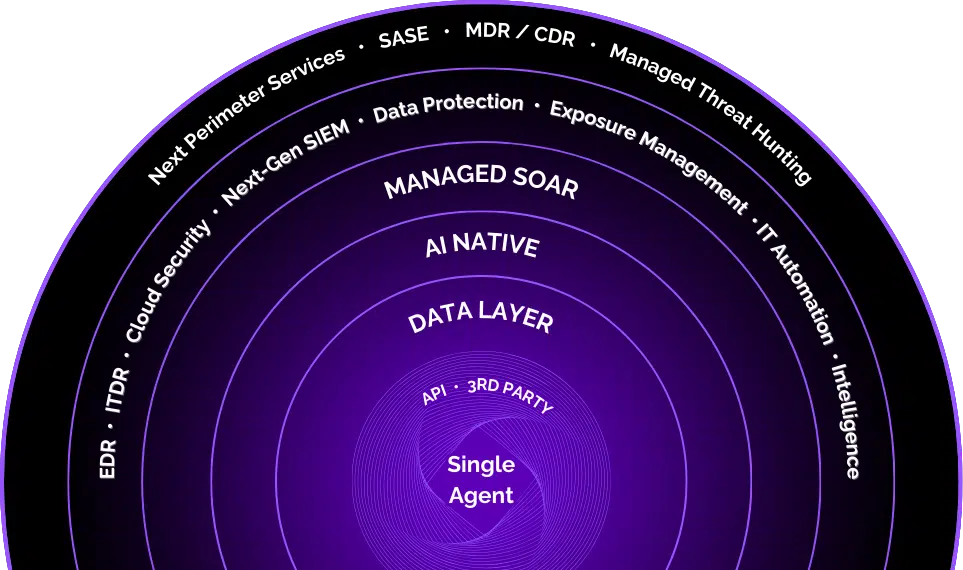
Protect Your Organization From Cyber Threats with SIEM & Threat Detection
Advanced Features to Strengthen Your Security
24/7 Security Monitoring
Round-the-Clock Security with Continuous Detection
Ensure your network is protected at all times with continuous monitoring that detects threats in real time. Next Perimeter’s 24/7 security monitoring provides vigilant oversight, allowing immediate response to potential risks, no matter the time of day
With our ongoing threat detection, your business remains secure and resilient against cyber threats.

Threat Intelligence Integration
Proactive Defense with Real-Time Insights
Stay ahead of emerging threats with real-time threat intelligence. By leveraging global insights through our advanced SIEM, Next Perimeter enhances your ability to detect and mitigate risks before they impact your operations.
Our proactive approach ensures that your defense strategy evolves as quickly as the threats you face.

Custom Dashboards and Reports
Tailored Insights for Strategic Decision-Making
Gain a clear and actionable view of your security landscape with custom dashboards and reports tailored to your specific needs. Next Perimeter allows you to monitor key metrics, track trends, and generate detailed insights that drive informed decision-making.
Empower your team with the insights they need to strategically manage and enhance your security posture.

Security That Grows with You
Adaptable Protection for Your Evolving Needs
As your business evolves, so do your security needs. Next Perimeter’s SIEM offers scalable and flexible protection that adapts effortlessly to your growth.
Whether you’re expanding operations or facing new challenges, our solution ensures your security infrastructure remains robust and responsive, without the need for complex adjustments.

Native Integrations with the Apps that Keep Your Business Running









READY TO TRANSFORM YOUR CYBERSECURITY?
Switching to Next Perimeter is Simple, with No Downtime or Disruptions
1. Free Exploratory Consultation Call
Let’s dive into your specific needs, security challenges, and current technology set-up. We’ll collaborate with you to start crafting tailored solutions that align with your business goals.

2. Identity & Device Assessment
Our experts will begin developing a customized proposal for your unique environment. We’ll perform a thorough assessment to finalize the scope, ensuring every aspect of your digital security is covered.

3. Schedule Your Seamless Onboarding
With your approval, we’ll launch your onboarding process. Our all-in-one security solution will seamlessly integrate into your existing infrastructure, implemented by our expert team for a smooth transition.
FAQ: Security Information & Event Management (SIEM)
Get answers to common questions about our SIEM solutions, threat detection, and how Next Perimeter can enhance your security strategy.
What is a SIEM solution?
A SIEM (Security Information and Event Management) solution is a system that collects, analyzes, and correlates security data from various sources within an organization’s IT infrastructure. It provides real-time monitoring, detection, and alerts for potential security threats, allowing organizations to detect and respond to incidents more efficiently. SIEMs are used to ensure compliance, monitor security risks, and manage incident response.
What is an example of a SIEM?
An example of a SIEM is Next Perimeter SIEM & Threat Detection, which is widely used to collect, monitor, and analyze security data. It helps organizations by offering real-time insights into their security posture and enabling faster detection and response to threats.
What are the three types of SIEM?
SIEM solutions can be categorized into three types based on their deployment models:
- On-premise SIEM: Installed and managed on the organization’s own servers. Suitable for organizations with strict data control requirements and huge budgets.
- Cloud-based SIEM: Hosted in the cloud, offering greater flexibility, scalability, and ease of use with lower upfront infrastructure costs.
- Hybrid SIEM: Combines both on-premise and cloud components, offering the advantages of both models, especially for organizations transitioning to the cloud or managing complex environments.
What is a SIEM vs a SOC?
A SIEM is a technology platform that collects and analyzes security data, while a SOC (Security Operations Center) is a dedicated team or facility that monitors and responds to security threats in real-time. A SOC uses a SIEM as one of its key tools to help detect and manage security incidents, but the SOC also involves people, processes, and other tools for incident response, threat hunting, and threat intelligence.
How is a SIEM service typically priced?
SIEM pricing is generally based on several factors, which can vary by provider:
- Log Data Volume: Many SIEM services charge based on the amount of data ingested per day (measured in gigabytes or terabytes).
- Number of Devices or Users: Some pricing models are based on the number of devices or users being monitored.
- Retention Period: SIEM services often have pricing tiers based on how long they store logs for compliance or auditing purposes
Next Perimeter’s pricing is device based offering unlimited storage at your tenants defined retention period, which could be considered a hybrid of two of the pricing modules below offering the most simplicity and predictability in the market today.
