Our Solutions
Fortified Security for Today’s Digital Landscape
In a world of evolving threats, Next Perimeter offers security solutions that go beyond the basics. Our layered defenses and zero trust framework ensure that your data, devices, and users are always protected—whether your team is working remotely or on-site.
Maximize Security and Productivity with Next Perimeter
At Next Perimeter, we believe security and productivity go hand in hand. Our advanced solutions not only protect your business from evolving cyber threats but also streamline operations, ensuring your team can work efficiently without compromising on safety. Experience peace of mind and enhanced performance with security that empowers your organization to thrive.
Enhanced Productivity Across Your Team
Empower your workforce with seamless technology that ensures they can work efficiently from any location. With simplified access to the tools they need, your employees stay connected, collaborative, and productive.
Comprehensive Security and Compliance
Our solutions offer protection and ensure compliance with regulations, safeguarding your data while simplifying management. With security built into every aspect of your infrastructure, you can focus on growing your business.
Tailored Solutions for Your Organization's Needs
Every business is different. That’s why we offer tailored solutions designed to align with your company’s requirements. From small teams to growing enterprises, we deliver solutions that evolve alongside your business.

97 Net Promoter Score®

2+ Million Incidents Resolved

4.9 Stars Average Ratings

4 Minute Average MTA

94.53% Same Day Resolution
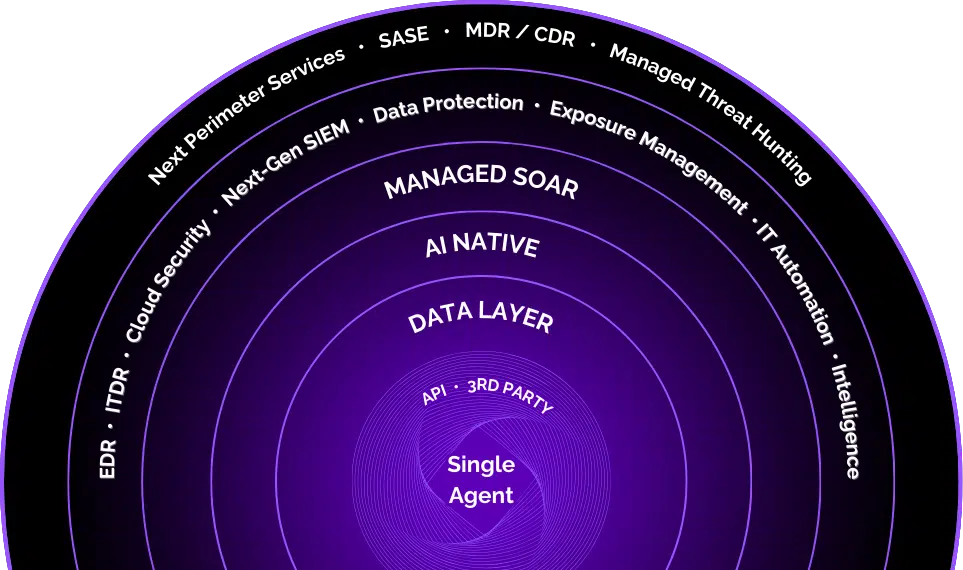
Achieve Total Security with Our Single-Agent Solution
Simplify your cybersecurity with a unified platform that combines advanced threat detection, data protection, and cloud security, ensuring seamless and comprehensive protection.
Modern Desktop Experience
Boost Productivity with a Secure Workstation
Next Perimeter’s Modern Desktop Experience ensures your team can work from anywhere with optimal security and efficiency. With pre-built templates, cloud integration, and always-on security, we streamline the user experience, allowing your employees to focus on work, not their tech.

Cloud Identity Management
Secure Access with Simple Identity Management
With Single Sign-On (SSO), Multi-Factor Authentication (MFA), and Role-Based Access Control (RBAC), our Cloud Identity Management solution makes securing user access easy and effective. Ensure your team’s productivity while safeguarding your business with streamlined identity control.

VPN Alternative
Always-On Security Without the Hassle of Traditional VPNs
Ditch outdated VPNs for our secure, cloud-based VPN alternative. Our SASE solution provides fast, reliable, and secure access for your team from anywhere, removing the headaches of slow connections and complex setups while keeping your business protected.

Microsoft 365 Blueprints
Streamline Your Security with Our Battle-Tested Microsoft 365 Blueprints
Optimize workflows, enhance data security, and ensure compliance with Next Perimeter’s pre-configured Microsoft 365 Blueprints. Our blueprints are ready to deploy, helping you unlock the full potential of Microsoft 365 without complex, custom setups.

Zero Trust Security
Protect Every Access Point with Zero Trust Security
Zero trust is a journey, and Next Perimeter’s solutions guide you through it with layered defenses, granular access controls, and always-on security. Our Zero Trust framework ensures that every user, device, and connection is verified, securing your business at every access point.

READY TO TRANSFORM YOUR CYBERSECURITY?
Switching to Next Perimeter is Simple, with No Downtime or Disruptions
1. Free Exploratory Consultation Call
Let’s dive into your specific needs, security challenges, and current technology set-up. We’ll collaborate with you to start crafting tailored solutions that align with your business goals.

2. Identity & Device Assessment
Our experts will begin developing a customized proposal for your unique environment. We’ll perform a thorough assessment to finalize the scope, ensuring every aspect of your digital security is covered.

3. Schedule Your Seamless Onboarding
With your approval, we’ll launch your onboarding process. Our all-in-one security solution will seamlessly integrate into your existing infrastructure, implemented by our expert team for a smooth transition.
