Microsoft 365 Blueprints
Battle-Tested Posture Management Configurations
Next Perimeter's Microsoft 365 Blueprints provide tailored configurations that enhance security, streamline operations, and ensure compliance. These pre-defined best practices are crafted to maximize your Microsoft 365 environment's performance, enabling your team to work smarter and more securely.
Unlock the Full Potential of Your Microsoft 365 Environment
Leverage the power of battle-tested Microsoft 365 Blueprints to secure your business, streamline compliance, and simplify your IT operations. Enjoy the peace of mind that comes with a solution designed to enhance your productivity while keeping your data protected.
Comprehensive Data Protection and Security
Keep your business safe with security settings that protect your data and systems. Our Microsoft 365 blueprints ensure continuous monitoring and remediation for deviations of your defined configuration baseline.
Easy and Effective Regulatory Compliance
Meet industry standards effortlessly while maximizing performance and productivity. Our Microsoft 365 blueprints follows NIST & Microsoft’s best practices for expertly configured security and configuration baselines.
Bespoke Workflows for Maximum Efficiency
Make your day-to-day IT processes smoother by unlocking the power of identity and device management features within your tenant. Our Microsoft 365 blueprints simplify processes and boost performance.

97 Net Promoter Score®

2+ Million Incidents Resolved

4.9 Stars Average Ratings

4 Minute Average MTA

94.53% Same Day Resolution
Achieve Total Security with Our Single-Agent Solution
Simplify your cybersecurity with a unified platform that combines advanced threat detection, data protection, and cloud security, ensuring seamless and comprehensive protection.
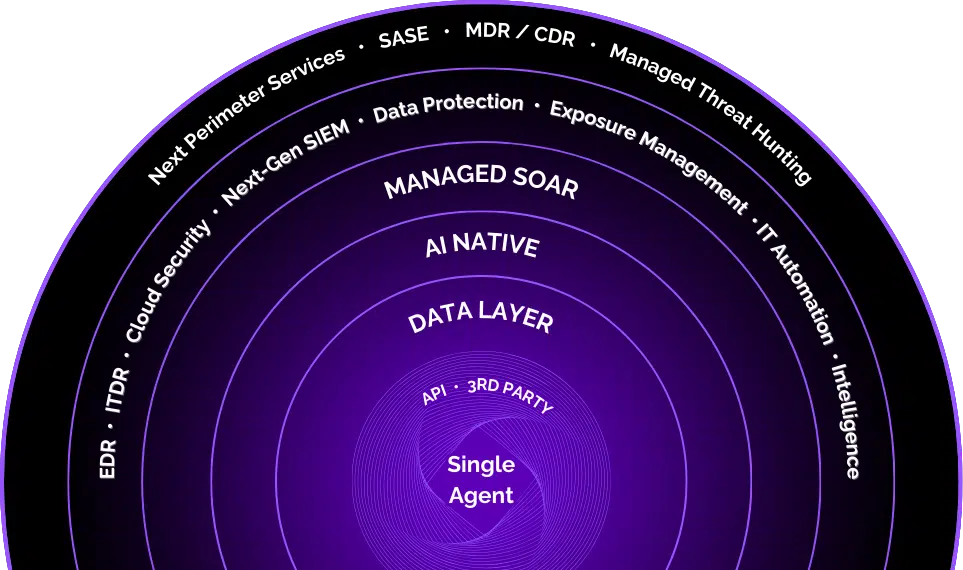
Tailored Configurations, Proactive Security, and Streamlined Compliance
Comprehensive & Secure Microsoft 365 Solutions
Security Posture Management
Enhanced Security and Risk Mitigation
As remote work and cloud strategies grow, keeping your digital environment secure is essential. Next Perimeter monitors your Microsoft 365 setup for risks and misconfigurations, quickly addressing security gaps.
We automate threat detection across devices, identities, and platforms to keep your business protected.

Proactive Threat Detection
Stay One Step Ahead of Cyber Threats
Our advanced threat detection system continuously scans for potential risks and cyber threats in real-time.
By identifying and addressing issues early, we prevent attacks from disrupting your operations, ensuring your business remains secure and productive in an ever-changing digital landscape.

Compliance Management
Regulatory Compliance and Auditing
Next Perimeter ensures your business stays compliant with regulations like HIPAA, PCI-DSS, and GDPR through continuous security monitoring.
We simplify complex compliance frameworks like NIST and ISO by automating best practices, reducing manual work, and ensuring you’re audit-ready.

Preconfigured Microsoft 365 Solutions
Proven Settings for Protection & Productivity
Our Microsoft 365 Blueprints come with preconfigured settings based on industry best practices, ensuring security and efficiency from day one.
These settings protect your data, streamline workflows, and boost productivity, minimizing manual setup and optimizing performance for your growing business.

READY TO TRANSFORM YOUR CYBERSECURITY?
Switching to Next Perimeter is Simple, with No Downtime or Disruptions
1. Free Exploratory Consultation Call
Let’s dive into your specific needs, security challenges, and current technology set-up. We’ll collaborate with you to start crafting tailored solutions that align with your business goals.

2. Identity & Device Assessment
Our experts will begin developing a customized proposal for your unique environment. We’ll perform a thorough assessment to finalize the scope, ensuring every aspect of your digital security is covered.

3. Schedule Your Seamless Onboarding
With your approval, we’ll launch your onboarding process. Our all-in-one security solution will seamlessly integrate into your existing infrastructure, implemented by our expert team for a smooth transition.
