VPN Alternative
Unshackle Your Business from VPNs
Say goodbye to restrictive VPN licensing and complex setups. With our single-agent security solution, there’s nothing more to install—ever. Enjoy seamless, always-on protection that simplifies remote access and eliminates the headaches of traditional VPNs. Empower your team with secure connectivity that just works, wherever they are.
Empower Your Team & Enhance Your Security, No VPN Required
Our VPN replacement is more than just secure connectivity — it’s about empowering your team to work efficiently and confidently, no matter where they are. Discover how our approach to remote access simplifies management, enhances productivity, and ensures that your business is always protected.
Always-On Protection From Anywhere in the World
Our solution provides continuous protection, so your team can work from anywhere without worrying about security. It’s designed to be straightforward and reliable, ensuring that secure access is always on, without the need for complex setups or logins.
Boost Team Productivity with Fast Connections
No more waiting on slow connections or dealing with frustrating interruptions. Our VPN replacement ensures your team stays connected with lightning-fast speeds so they can focus on achieving their goals without technical distractions.
Stay Secure Without the Need for Firewalls
Managing remote access shouldn’t mean juggling firewalls. When your endpoints join our platform, they’re not just connecting to a VPN—they’re securely authenticating to the world. Our platform keeps your team constantly defended, making security effortless and worry-free.

97 Net Promoter Score®

2+ Million Incidents Resolved

4.9 Stars Average Ratings

4 Minute Average MTA

94.53% Same Day Resolution
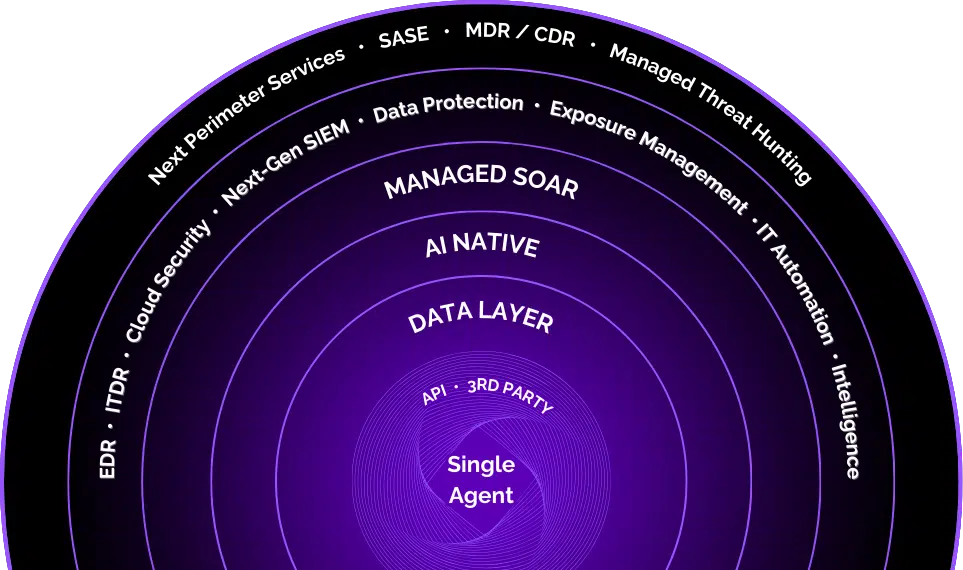
Achieve Total Security with Our Single-Agent Solution
Simplify your cybersecurity with a unified platform that combines advanced threat detection, data protection, and cloud security, ensuring seamless and comprehensive protection.
Redefine Remote Access with Seamless Security
Stay Connected & Protected — Anytime, Anywhere
Zero Trust Security Model
Authenticate Every User and Every Device
With our Zero Trust Security Model, every user and device is verified before gaining access to your network.
This approach ensures that only authorized personnel can interact with your sensitive data, reducing the risk of breaches and creating a more secure environment for your business, no matter where your team works.

Seamless Integration
Enhance Security Without the Disruption
Integrating new security measures shouldn’t interrupt business operations or slow down your team.
Next Perimeter’s VPN alternative fits effortlessly into your current systems, providing enhanced protection without the need for complex migrations or operational disruptions. Enjoy stronger security without any downtime.

Multi-Factor Authentication (MFA)
Simple Verification for Stronger Protection
Multi-factor authentication adds an additional layer of security to your team’s remote access.
By requiring users to verify their identity through multiple steps, our solution ensures that unauthorized users are kept out — even if passwords are compromised. It’s a simple, effective way to protect your business.

Continuous Monitoring & Analytics
Proactively Detect Threats in Real Time
Stay ahead of potential cyber threats with continuous, real-time monitoring of your network.
Our analytics provide deep insights into user activity and security events, allowing you to spot and address suspicious behavior before it becomes a problem. Proactive protection keeps your business secure around the clock.

User-Friendly Experience
Streamlined Security and Hassle-Free Access
Security shouldn’t slow down your team. Our VPN replacement is designed with simplicity in mind, providing an intuitive, user-friendly experience that makes secure access easy for everyone.
With hassle-free deployment and effortless day-to-day use, your team can stay productive without worrying about complex security protocols.

Native Integrations with the Apps that Keep Your Business Running









READY TO TRANSFORM YOUR CYBERSECURITY?
Switching to Next Perimeter is Simple, with No Downtime or Disruptions
1. Free Exploratory Consultation Call
Let’s dive into your specific needs, security challenges, and current technology set-up. We’ll collaborate with you to start crafting tailored solutions that align with your business goals.

2. Identity & Device Assessment
Our experts will begin developing a customized proposal for your unique environment. We’ll perform a thorough assessment to finalize the scope, ensuring every aspect of your digital security is covered.

3. Schedule Your Seamless Onboarding
With your approval, we’ll launch your onboarding process. Our all-in-one security solution will seamlessly integrate into your existing infrastructure, implemented by our expert team for a smooth transition.
