Zero Trust Security
Fortify Your Business with Zero Trust Security
Zero trust is more than just a security model—it's a mindset that requires a proactive and evolving approach to safeguarding your business. At Next Perimeter, we understand that achieving zero trust takes time and effort. Our solutions are designed to guide you through each stage of this journey, providing the tools, technology, and expertise necessary to secure your network, users, and data.
Experience the Benefits of Zero Trust Protection
Zero trust security creates a stronger, more resilient defense by continuously verifying every user and device in your network. With Next Perimeter’s tailored solutions, your business will benefit from an adaptive security model designed to protect every user, device, and connection. Embrace zero trust and experience the difference in security, efficiency, and confidence.
Progressive Security, Tailored to Your Business
Implementing zero trust is a step-by-step process that begins with understanding your current vulnerabilities. Next Perimeter assesses your environment and customizes security solutions that lay the groundwork for a stronger security posture—whether you’re just starting or seeking to enhance an existing strategy.
Proactive Defense Against Evolving Threats
Zero trust is designed to stay ahead of cyber threats, limiting access and verifying every request. We implement tools such as MFA, network segmentation, and continuous monitoring, creating an ever-evolving perimeter that adapts to new threats. Every access request is verified, keeping your sensitive data out of the wrong hands.
Achieve Long-Term Compliance & Security Goals
Zero trust simplifies your journey to compliance while ensuring your business stays protected at every stage. Many regulatory requirements align with the zero trust framework. With our solutions, you’ll not strengthen security and streamline your path toward meeting compliance standards like HIPAA, SOC2, and more.

97 Net Promoter Score®

2+ Million Incidents Resolved

4.9 Stars Average Ratings

4 Minute Average MTA

94.53% Same Day Resolution
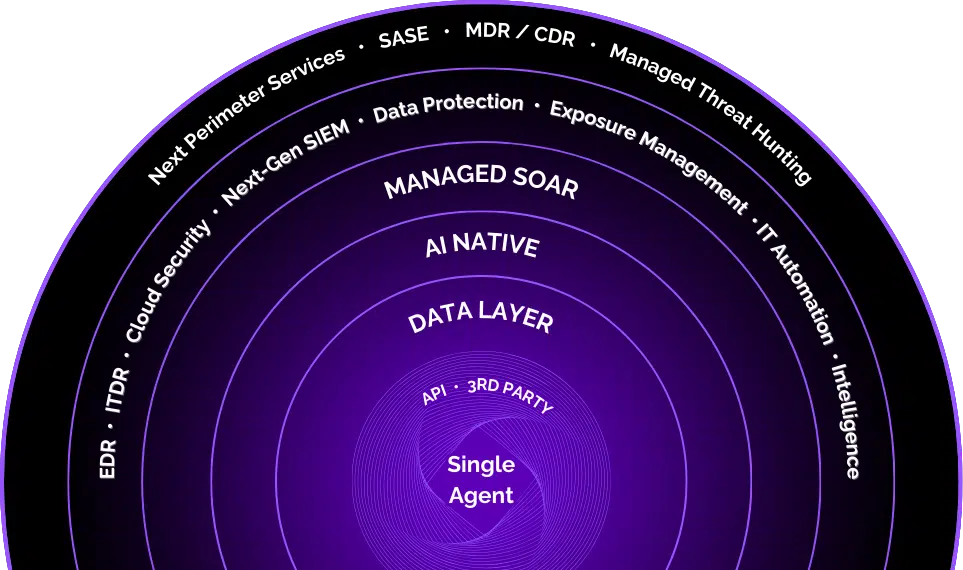
Achieve Total Security with Our Single-Agent Solution
Simplify your cybersecurity with a unified platform that combines advanced threat detection, data protection, and cloud security, ensuring seamless and comprehensive protection.
Identity Verification at Every Step
Secure Every User & Device Across Your Network
Next Perimeter ensures that every user and device is thoroughly verified before gaining access to your network.
By implementing tools like Multi-Factor Authentication (MFA) and Single Sign-On (SSO), we provide robust identity management that keeps unauthorized access at bay. This ensures that only the right people have access to your critical systems.

Granular Access Controls
Limit Access & Strengthen Your Cyber Defenses
With Next Perimeter’s Zero Trust Network Access, you can define precise access controls for every user and device.
By implementing Role-Based Access Control (RBAC) and least privilege policies, we minimize lateral movement within your network. This significantly reduces potential risks and enhances your overall security posture.

Continuous Monitoring and Alerts
Stay Ahead of Threats with Real-Time Detection
Our solutions provide real-time monitoring and threat detection, ensuring that suspicious activity is flagged and dealt with immediately.
By continuously tracking behavior across your network, we can detect potential breaches before they cause damage. This proactive approach keeps your business safe from evolving threats.

Seamless Integration
Easily Protect Your Existing Systems and Applications
Next Perimeter’s zero trust solutions integrate easily with your current infrastructure, allowing for a smooth transition without disruptions.
Whether you use cloud platforms like Microsoft 365 or on-premise systems, our security seamlessly protects your operations. This ensures continuous security while maintaining your team’s productivity.

Native Integrations with the Apps that Keep Your Business Running









READY TO TRANSFORM YOUR CYBERSECURITY?
Switching to Next Perimeter is Simple, with No Downtime or Disruptions
1. Free Exploratory Consultation Call
Let’s dive into your specific needs, security challenges, and current technology set-up. We’ll collaborate with you to start crafting tailored solutions that align with your business goals.

2. Identity & Device Assessment
Our experts will begin developing a customized proposal for your unique environment. We’ll perform a thorough assessment to finalize the scope, ensuring every aspect of your digital security is covered.

3. Schedule Your Seamless Onboarding
With your approval, we’ll launch your onboarding process. Our all-in-one security solution will seamlessly integrate into your existing infrastructure, implemented by our expert team for a smooth transition.
