Protect your assets with advanced IT security.
We utilize industry-leading measures to develop an extensive security strategy that includes network segmentation, systems implementations, testing, 24/7 monitoring, vulnerability and patch management, as well as compliance audits to ensure your company doesn’t face a crippling threat event.
Stay ahead of cybercrime with ITSG security protection.

Discover the benefits of Managed Security Services
Cybercrime is Always Evolving.
Your Cybersecurity Should Too.
Staying ahead of cybercrime requires an approach custom-made to your business. Our experts equip companies with proactive IT security services plans designed to keep hackers at bay.

Managed Security Services + More
With our Copilot Protect plan, your business is protected to the fullest extent, and you’ll receive all Managed IT Services featured in the Copilot Essential plan.
Our Managed Security Services include:
- 24/7 SOC + MXDR + SIEM
- CIO Quarterly Business Reviews
- Employee Security Awareness Training
- Compromised user detection
- Unlimited help desk support
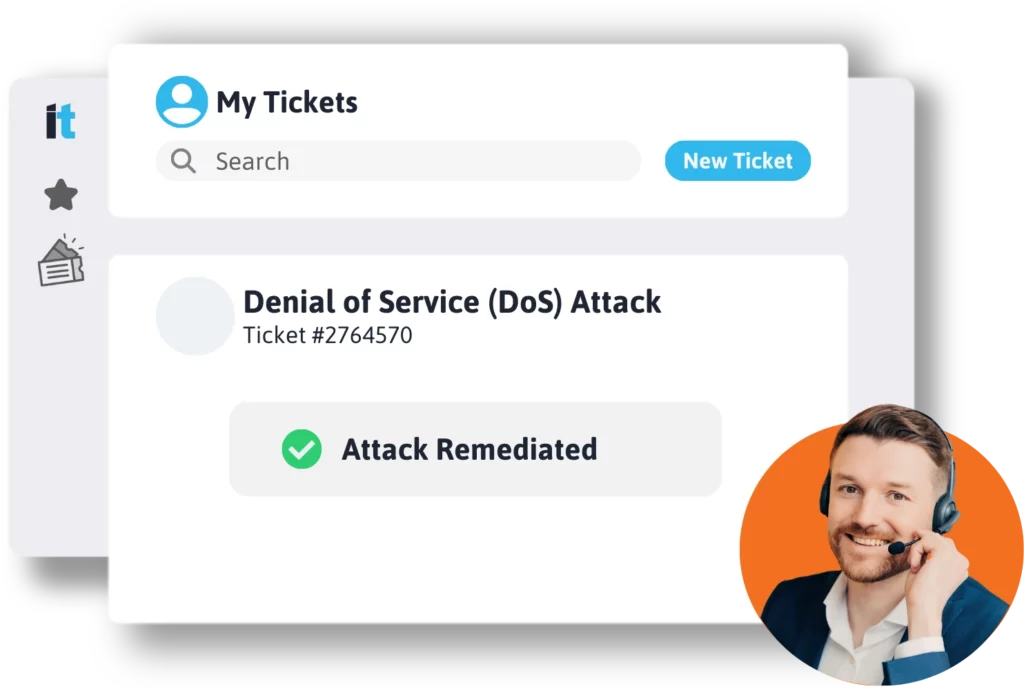
Around the Clock Security Protection & Management
More than 43 percent of cyberattacks target small businesses, with 94 percent of malware delivered via email.
That’s why endpoint security is crucial.
Managed Endpoint Security involves proactively detecting and responding to advanced security threats like malware, ransomware, phishing, social engineering campaigns, and even combats insider threats looking to steal intellectual property or company assets.
IT Support Guys’ endpoint protection platform (EPP) is a solution deployed on endpoint devices to prevent file-based malware attacks, detect malicious activity, and provide the investigation and remediation capabilities required to respond to dynamic security incidents and alerts.
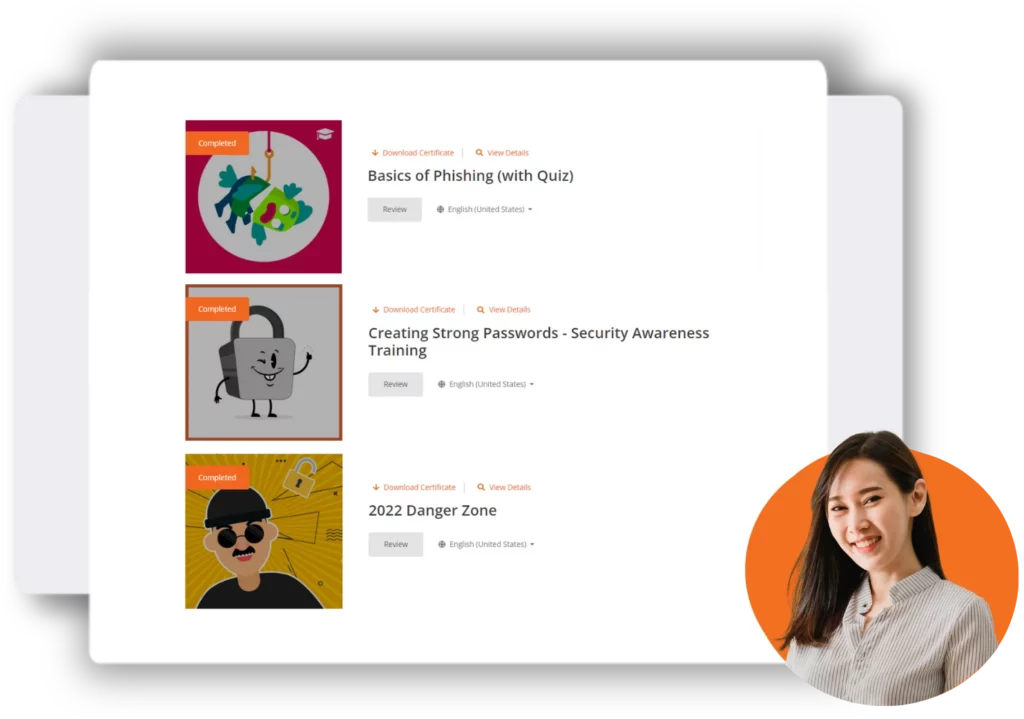
Employee Security Awareness Training
We partnered with KnowBe4 to help inform your employees on the importance of security protection.
Over 91 percent of cyberattacks begin with a phishing email. Scarier yet is the fact that 62 percent of phishing simulations capture at least one user’s credentials. Security is now a top priority for everyone – from the average consumer to the biggest enterprises.
Inadequate email security measures will inevitably lead to a breach sooner or later. ITSG’s email security services grant you protection from ransomware, malware, phishing attempts, and other email threats.
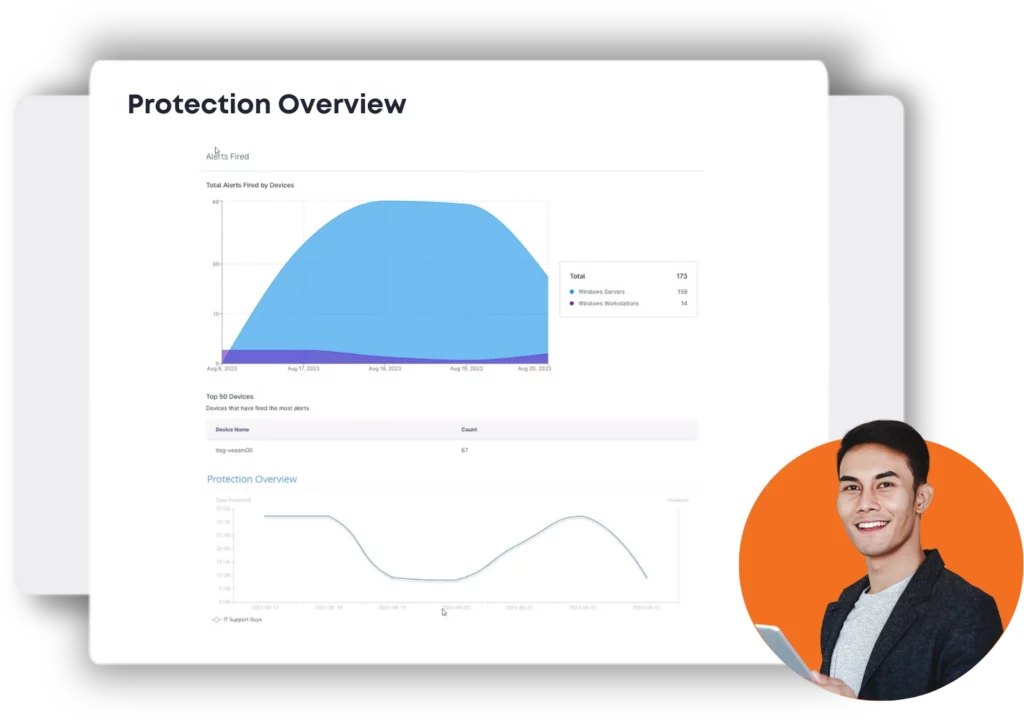
Analyze and Manage Security Threats with SIEM
Security Information and Event Management (SIEM) is a solution that combines and analyzes activity from different sources across your entire IT infrastructure. IT Support Guys will discover trends, detect insider threats or potential cyberattacks, and investigate cybersecurity alerts.
Our endpoint security and monitoring services help to protect the IT infrastructure of your company. Whether we’re defending against threats, setting up employee monitoring applications, or protecting sensitive information, our SIEM approach is crucial to a safe and secure business.
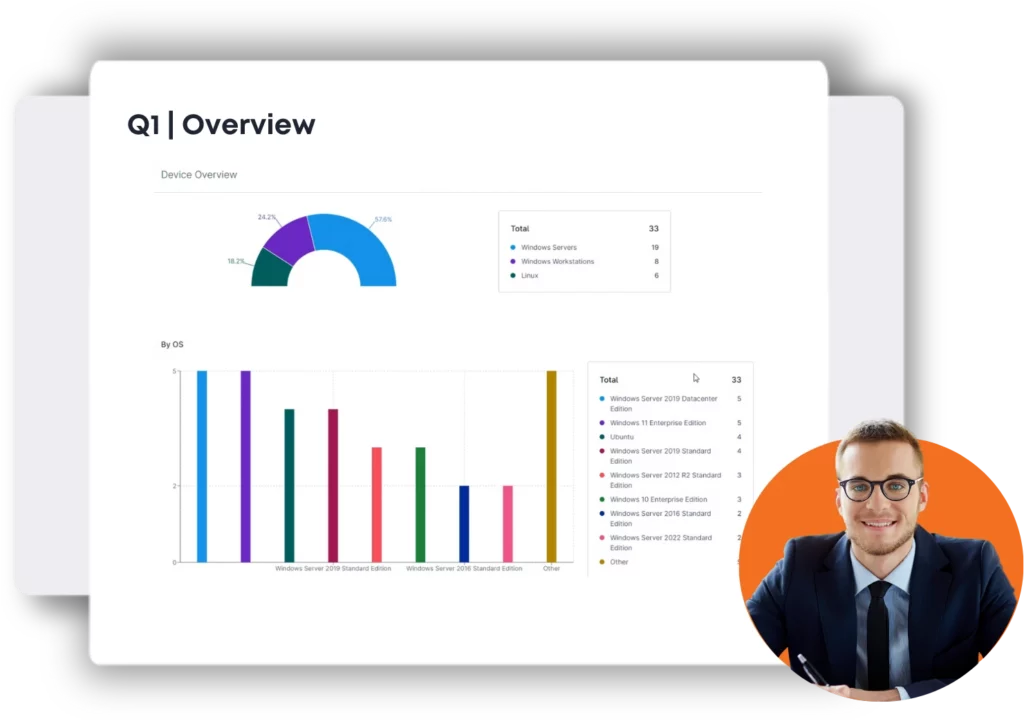
Quarterly Business Reviews with a CIO
Our quarterly business reviews keep you in the loop on everything going on with your business IT. We keep organized logs of every helpdesk ticket submitted, security breach, and more.
A Chief Information Officer (CIO) will help your organization with overseeing, developing, and managing your overall technology strategy, innovation, and IT infrastructure. The CIO ensures that you stay up to date on the latest technological advancements and trends.
Our Security Features
Take detection and response to the next level with continuous 24/7 protection. We will investigate every alert for suspicious activity, isolate hosts, if compromised, and notify you only when a threat is real.
Your CIO will work cross-functionally to support your business goals. Going beyond just insights into your environment, the CIO will assist with planning, budgeting, managing, and reporting on IT for your business.
ITSG handles all of the licensing, administration, group management, training video selection, and more. Leverage our industry benchmarks to ensure your security training program adheres to best practices and meets compliance requirements.
Real techs on speed dial. No automated systems or offshore teams reading scripts. Unlimited driver updates, issue resolution, and remote troubleshooting for your workstations, SaaS, and the Cloud IDs therein.
Impossible travel alerts. Geofencing. Our systems catch imposters and bad actors in the act, based on flagged behaviors. Our cloud identity protection service is unrivaled.
Put down the storage cost calculator. It’s not a matter of if, it’s a matter of when you’ll need a restore. We make sure all important data is backed up, monitored, and available when you need to restore it. (With military-grade encryption!)
Are disks filling up or dying?
We’ll hear about it and call you before you notice. Our experts flag assets near end-of-life and help you replace them. Avoid downtime, improve performance, and extend the lifespan of all your important systems.
Your OS and third-party apps are always at their safest. We make sure updates are deployed successfully and at a time that won’t slow you down. Check-off-boxes on those pesky cybersecurity questionnaires.
Leverage our experience over thousands of deployments for best-in-class purchases that won’t frustrate you. We partner with the most trustworthy, innovative names in tech. Plus, we will handle communication for you.
Great documentation is the secret weapon of great IT service. We write and keep your docs updated for you – speeding up issue resolution, ensuring on-time license renewals, and more.
You need your endpoints to stay working. We’ll get a tech to your door within a business day – anywhere in the US when following our design recommendations.
Flexible Hybrid Plans Based on Identities and Devices.
Identity Protection & Support
Need essential cloud identity protection and support for your users?
Your cloud identities (and users) will receive unlimited cloud support, backups, and compromised user protection.
Device Protection & Support
Need IT services to support your workstations?
Gain access to best-in-class Endpoint Protection & Response, Next Gen Antivirus, Patch Management, Proactive Performance & Management, Warranty management and much more.
Identity & Workstation Protection & Support Bundle
The best of both worlds!
The ideal setup for most organizations. One computer per agent, with all of the essential security out of the box for both. The bundle unlocks the full range of features for your team.